Table of Contents
Home / Blog / Cryptocurrency
Security First DEX Development: How to Build Trust in Decentralized Trading
November 15, 2025

November 15, 2025
Decentralized exchanges (DEXs) are reshaping the global cryptocurrency market, giving users full control over their assets without intermediaries. In September 2025, perpetual DEXs recorded a trading volume of $1.14 trillion, crossing the $1 trillion mark for the first time. During the same period, spot trading on DEXs climbed to $876.3 billion, reflecting a 25.3% quarterly rise. These numbers highlight a clear shift toward decentralized trading and greater demand for transparency.
As adoption grows, building trust becomes vital. A security-first approach to DEX development ensures reliable smart contracts, mitigates vulnerabilities, and establishes long-term credibility within the rapidly expanding DeFi ecosystem.
In this piece, we will guide you through the essentials of DEX development, including its core features, benefits, security challenges, emerging technologies, and how to build secure and credible DEXs from the ground up.
Build a DEX That Traders Trust
Launch your decentralized exchange with top-tier security architecture and seamless user experience. We design systems built to earn user confidence from day one.
What Is DEX Development?
Decentralized Exchange (DEX) development involves creating blockchain-based trading platforms that eliminate the need for intermediaries, thereby enhancing the efficiency of trading. These platforms allow users to trade cryptocurrencies directly from their wallets through automated smart contracts. Unlike centralized exchanges that hold users’ funds, DEXs prioritize transparency, on-chain settlement, and user autonomy.
Developers or crypto exchange development companies focus on building infrastructure that supports peer-to-peer trading, efficient liquidity mechanisms, and strong security models. As decentralized finance (DeFi) continues to expand, the demand for decentralized trading platforms built on scalable, secure, and interoperable architectures has grown significantly.
Benefits of DEX Development
DEX development delivers far more than decentralized trading. It introduces efficiency, transparency, and financial independence, empowering users to trade securely without relying on centralized intermediaries.
1. Enhanced User Control
DEX platforms allow users to trade directly from their personal wallets, ensuring complete custody of funds at all times. This eliminates the risks tied to centralized storage breaches, withdrawal freezes, or exchange mismanagement. By maintaining control over their private keys, users achieve genuine financial autonomy within a trustless trading ecosystem.
2. Transparency and Auditability
Every transaction, liquidity movement, and contract execution on a decentralized exchange software is recorded immutably on the blockchain. This transparency allows users and auditors to verify activity independently, promoting trust and accountability. Open access to on-chain data ensures that no hidden manipulation or unauthorized transactions occur within the platform’s ecosystem.
3. Lower Entry Barriers
Unlike centralized exchanges that require extensive registration and verification, DEXs enable permissionless access. Users can trade seamlessly across borders without identity restrictions. This inclusivity promotes financial freedom and supports users in regions underserved by traditional finance, expanding market participation and enabling more equitable access to digital assets.
4. Resilience Against Centralized Failures
Since DEXs operate on distributed nodes across multiple validators, they remain functional even if some nodes go offline. This decentralized infrastructure prevents single points of failure, censorship, and forced shutdowns, ensuring continuous trading access regardless of political, technical, or regulatory disruptions that may affect centralized exchange operators.
5. Rapid Innovation and Integration
The open-source nature of DEX protocols allows developers to integrate new features, plug-ins, or DeFi tools quickly. This flexibility encourages experimentation, interoperability, and cross-protocol collaboration. Continuous innovation enables platforms to adapt to changing market needs while maintaining strong liquidity and competitive transaction efficiency within the broader DeFi ecosystem.
Also Read: DEX Aggregators vs. Standalone Decentralized Exchanges: Key Differences
Key Features of DEX Development
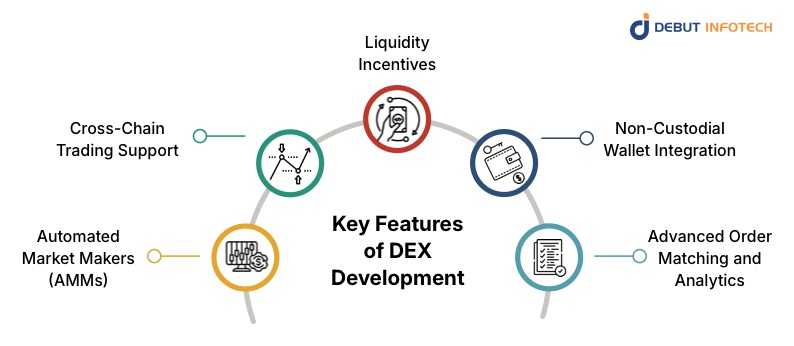
1. Automated Market Makers (AMMs)
AMMs replace traditional order books by automatically calculating prices through algorithmic formulas. Liquidity providers deposit tokens into pools, earning fees from every trade that occurs. This system ensures continuous trading activity, enhances liquidity availability, and minimizes slippage, thereby creating a fair and efficient trading environment for users worldwide.
2. Cross-Chain Trading Support
Modern DEXs integrate cross-chain bridges that connect different blockchain networks, enabling users to trade tokens from Ethereum, Solana, BNB Chain, and other networks in a single interface. This feature expands market accessibility and asset diversity, enabling true interoperability and a seamless user experience across multiple blockchain ecosystems.
3. Liquidity Incentives
To maintain deep liquidity, DEXs reward users who provide funds to trading pools through yield farming, staking, or liquidity mining. These incentive models help sustain healthy market volumes and reduce volatility. Users earn passive income, while the platform benefits from consistent liquidity and price stability.
4. Non-Custodial Wallet Integration
DEXs enable users to connect decentralized wallets, such as MetaMask, WalletConnect, or Trust Wallet, to trade directly without depositing assets on the platform. This structure removes custodial risk and ensures complete privacy. Users retain ownership of their private keys, enhancing both transparency and long-term asset security.
5. Advanced Order Matching and Analytics
High-performing DEXs use smart algorithms to match orders efficiently, minimizing delays and optimizing trade execution. Real-time analytics dashboards track liquidity trends, token prices, and user activity, providing traders with valuable insights for informed decision-making. This combination of automation and data visibility improves trading accuracy and user experience.
What Is Security-First DEX Development?
Security-first DEX development refers to designing decentralized exchanges with cybersecurity as a primary objective—not an afterthought. It means embedding advanced protection layers into every stage of the development cycle, from smart contract design to post-launch monitoring and maintenance. This approach ensures that traders can engage in secure transactions without fearing exploits, flash loan attacks, or liquidity drain. By integrating audits, compliance standards, and adaptive security mechanisms, developers build a decentralized crypto exchange architecture that safeguards both assets and user trust.
Why Security Is the Foundation of DEX Credibility
Security defines a DEX’s reputation. Without strong protective measures, even the most advanced exchanges risk losing user confidence and market relevance. Here’s why it forms the foundation of credibility:
1. Asset Protection
Users trust DEXs to safeguard digital assets worth millions of dollars. A single exploit or liquidity drain can destroy that trust overnight. Strong encryption, secure smart contract architecture, and continuous audits ensure funds remain protected, reinforcing the DEX’s reliability and preserving investor confidence in decentralized trading environments.
2. Code Integrity
DEXs operate entirely on smart contracts, which must execute flawlessly. Compromised or unaudited code can expose hidden backdoors. Conducting multiple security audits, integrating bug bounty programs, and implementing formal verification techniques preserve code integrity, guaranteeing fair trade execution and protecting users from manipulation or malicious activities.
3. Reputation and Longevity
A DEX’s survival depends on its reputation. Once breached, user trust is almost impossible to rebuild. Top decentralized exchanges or platforms that prioritize security through proactive audits, transparency reports, and ongoing protection measures maintain credibility, attract long-term users, and remain competitive within the increasingly crowded decentralized finance marketplace.
4. Regulatory Confidence
Regulators are becoming more attentive to DeFi platforms. A security-focused DEX that adheres to compliance requirements and demonstrates strong user protection measures attracts institutional participation. Transparent governance, proper audit trails, and adherence to anti-money laundering (AML) standards help bridge the gap between decentralized innovation and regulatory acceptance.
5. User Retention
In decentralized trading, user loyalty is largely dependent on trust. When users feel secure, they are more likely to reinvest and participate in liquidity programs. Ongoing transparency, responsive threat mitigation, and a proven record of safety turn first-time traders into long-term users, strengthening community engagement and ecosystem stability.
6. Network Stability
A secure DEX prevents disruptions from malicious actors attempting to exploit consensus mechanisms or overload network nodes. By using distributed validation, automated fail-safes, and consistent patch updates, developers ensure continuous uptime. This operational stability reinforces platform reliability, attracting both institutional and retail traders seeking dependable trading infrastructure.
Core Security Challenges in DEX Development
1. Smart Contract Vulnerabilities
Smart contracts automate trades but are highly sensitive to coding errors. A single vulnerability can lead to flash loan exploits or unauthorized withdrawals of funds. Developers must conduct multiple code reviews, formal verifications, and continuous monitoring to identify weaknesses before deployment and protect users from devastating financial losses.
2. Liquidity Pool Risks
Liquidity pools can be targeted through price manipulation or oracle exploits, resulting in a significant capital drain. Developers or decentralized crypto exchange development companies integrate reliable oracles, dynamic pricing mechanisms, and circuit breakers to prevent such attacks. Maintaining healthy liquidity distribution across pools is vital for stabilizing token prices and preserving market fairness.
3. Private Key Management
Private keys are gateways to user funds. Poor storage or exposure to malware can lead to irreversible losses. Implementing Multi-Party Computation (MPC), hardware security modules (HSMs), and secure recovery protocols ensures that no single entity controls private keys, drastically reducing the risks of theft and unauthorized transactions.
4. API and UI Exploits
Attackers often target the API and front-end layers to inject malicious code or deceive users with phishing interfaces. Securing endpoints through authentication layers, encrypted communication, and regular testing minimizes these risks. A secure UI and API structure maintains user confidence and guarantees a seamless trading experience.
Emerging Security Technologies for DEXs
1. Zero-Knowledge Proofs (ZKPs)
Zero-Knowledge Proofs support blockchain transaction validation without revealing sensitive information. This technology enhances privacy by confirming data authenticity without direct disclosure. For decentralized exchanges for trading crypto assets, ZKPs provide secure verification for swaps, balances, and liquidity actions while maintaining anonymity—ensuring both compliance and user confidentiality in decentralized environments.
2. Multi-Party Computation (MPC)
Multi-party computation divides cryptographic key management across multiple nodes, ensuring that no single party holds complete access. This decentralized security approach minimizes the risk of theft, compromise, or collusion. In DEX infrastructure, MPC strengthens wallet security, streamlines multi-signature operations, and supports secure asset transfers under fully encrypted, trust-minimized conditions.
3. AI-Powered Threat Detection
Artificial intelligence continuously monitors smart contracts to detect irregularities or unusual trading behaviors. By analyzing historical patterns and network activity, AI identifies early signs of attacks such as flash loans or price manipulation. These predictive models enable faster responses, significantly reducing the window for exploit execution on DEX platforms.
4. Real-Time Anomaly Detection
Anomaly detection tools use behavioral analytics to identify suspicious wallet activities, irregular transactions, or contract interactions. When deviations from normal patterns occur, alerts trigger immediate investigation or automated countermeasures. Real-time defense systems help maintain transaction integrity and protect decentralized liquidity pools against coordinated, large-scale exploit attempts.
Building a Security-First DEX: Step-by-Step Approach
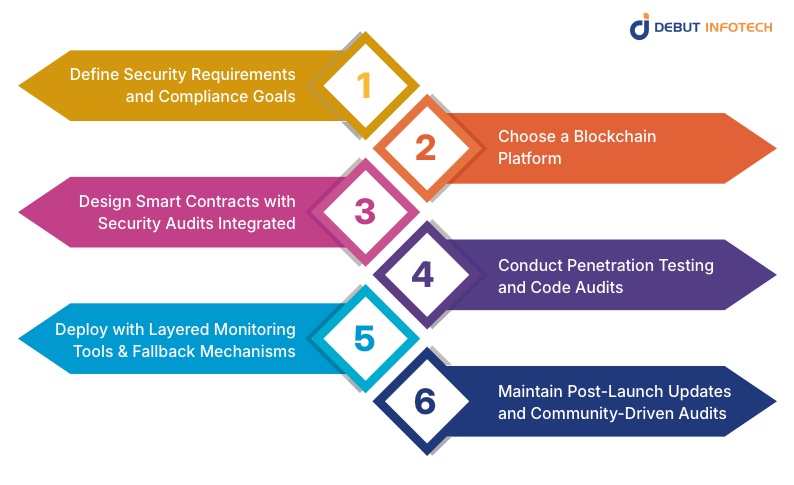
1. Define Security Requirements and Compliance Goals
The first step involves outlining precise security policies that cover access control, encryption standards, and compliance frameworks, such as AML or KYC. Establishing these benchmarks early ensures a structured foundation for risk mitigation, regulatory alignment, and adherence to best practices throughout the DEX’s entire development and operational lifecycle.
2. Choose a Blockchain Platform
Selecting the right blockchain is crucial for achieving scalability, interoperability, and security. Ethereum, BNB Chain, and Solana each offer distinct advantages in terms of transaction speed, developer tools, and audit readiness. The chosen platform should align with performance goals, governance models, and community support to ensure long-term sustainability.
3. Design Smart Contracts with Security Audits Integrated
Smart contract design must incorporate secure coding principles and independent audits from the outset. Developers or companies providing decentralized exchange development services integrate static analysis tools, formal verification, and peer reviews to ensure quality. By embedding audits during development, vulnerabilities are detected early, reducing post-deployment risks and ensuring smart contracts operate exactly as intended.
4. Conduct Penetration Testing and Code Audits
Penetration testing replicates real-world cyberattacks to identify weak points in infrastructure and code. Regular code audits validate that contracts, APIs, and data flows are secure. This process helps uncover hidden vulnerabilities, ensuring DEX systems remain resistant to both automated exploits and human-engineered intrusion attempts.
5. Deploy with Layered Monitoring Tools and Fallback Mechanisms
Upon deployment, DEXs integrate multi-layered monitoring systems that oversee smart contract activity, network health, and liquidity flow. Automated fail-safes pause trading or isolate contracts if anomalies arise. These protective mechanisms minimize downtime, maintain transparency, and uphold user confidence during unexpected or malicious events.
6. Maintain Post-Launch Updates and Community-Driven Audits
Security management continues beyond launch. Frequent updates patch vulnerabilities and strengthen defense layers. Encouraging community-driven audits, bug bounty programs, and open-source collaboration ensures continuous improvement. This collective vigilance builds a sustainable security culture that keeps the DEX adaptive, resilient, and aligned with evolving cyber threats.
Why It Is Crucial to Partner with a Security-Focused DEX Development Company
1. Expertise in Blockchain Security
Security-focused DEX developers possess specialized knowledge of smart contract auditing, encryption methods, and blockchain-based defense models. Their deep understanding of DeFi attack vectors—such as flash loan exploits or reentrancy bugs—ensures proactive risk prevention. Partnering with experts reduces vulnerabilities, promotes platform resilience, and guarantees user protection from sophisticated threats.
2. Reputation and Accountability
Partnering with an established cryptocurrency exchange development company offers more than technical expertise—it provides long-term accountability. Reputed firms maintain strict documentation, transparent communication, and post-launch support. Their professional credibility strengthens investor trust, enhances market reputation, and ensures the DEX continues to meet industry security benchmarks over time.
3. End-to-End Compliance Support
Regulatory compliance is essential for credibility. Security-oriented firms integrate AML, KYC, and GDPR frameworks within DEX architectures. They ensure smart contracts and APIs comply with international standards, enabling smooth interactions with institutional investors and regulators. This alignment fosters transparency, user confidence, and cross-border operational legitimacy.
4. Customizable and Audited Smart Contracts
A security-driven DEX development company builds modular smart contracts that undergo multiple layers of independent audits. These reusable components minimize human error and mitigate risks. Developers test contract logic rigorously, ensuring high transaction accuracy, efficient performance, and long-term security across diverse DeFi integrations and liquidity mechanisms.
5. 24/7 Threat Monitoring and Maintenance
DEX platforms require constant oversight to detect and neutralize emerging threats. Specialized development partners implement AI-powered security dashboards, automated alerts, and continuous code analysis to enhance security. This proactive surveillance identifies vulnerabilities in real-time, ensuring uninterrupted operations and protecting user assets against evolving cyber threats.
Looking to Partner with A Top-tier Company in Security-First DEX Development?
When it comes to building decentralized and secure blockchain exchanges that inspire user confidence, Debut Infotech stands out for one simple reason — security is never an afterthought. We offer DEX development services and design every DEX solution with built-in defense mechanisms, rigorous audits, and proactive monitoring, ensuring users trade with full assurance and zero compromise on safety.
From smart contract verification to real-time threat monitoring, every stage of development emphasizes protection and compliance. With a proven record in delivering secure, scalable DeFi platforms, we help businesses earn user confidence and sustain growth in competitive markets. Our commitment to transparency, reliability, and innovation makes us a dependable partner for security-focused DEX development.
Scale Without Compromising Safety
We design DEXs that handle high transaction volumes while keeping your assets and data locked behind solid security protocols.
Conclusion
Security-first DEX development builds more than just a decentralized platform—it builds trust and long-term sustainability. As trading volumes continue to surge and DeFi ecosystems mature, users expect transparency, resilience, and accountability from every protocol they engage with.
Platforms that integrate continuous audits, real-time monitoring, and multi-layered protection foster lasting user confidence. Since the market is driven by trust and technology, prioritizing security from the outset ensures your decentralized exchange not only survives volatility but also thrives as a credible, future-ready DEX solution.
FAQs
A. DEX platforms utilize AI-powered analytics, on-chain monitoring tools, and automated anomaly detection to track suspicious transactions in real-time. Smart contract auditing tools, such as MythX or Slither, also flag vulnerabilities early. Meanwhile, KYC integration and transaction safelisting help prevent wallet-level fraud and malicious activities.
A. Smart contract bugs, flash loan exploits, and front-running attacks are common weak points in DEX development. Others include faulty oracle integrations, liquidity pool manipulation, and inadequate key management. These flaws often come from rushed audits or poor coding practices, which attackers can exploit for quick financial gain.
A. Developers should follow OWASP standards, use secure smart contract frameworks, and implement multi-sig wallets for fund protection. Regular audits, KYC/AML compliance, and adherence to ISO/IEC 27001 guidelines also strengthen DEX security. These steps ensure code integrity, reduce risk exposure, and build user confidence in the platform.
A. A security-focused DEX can cost anywhere from $80,000 to $250,000, depending on the scope, tech stack, and features. Factors such as multi-chain support, audit depth, and UI complexity can increase the cost. It’s a serious investment, but cutting corners on security usually costs more in the long run.
A. A secure DEX usually takes four to eight months to build. The timeline depends on the project size, blockchain compatibility, and security integration requirements. The development phase encompasses design, coding, auditing, and extensive testing prior to launch. Rushing the process increases risks, so quality control is key throughout.
Talk With Our Expert
Our Latest Insights
USA
2102 Linden LN, Palatine, IL 60067
+1-708-515-4004
info@debutinfotech.com
UK
Debut Infotech Pvt Ltd
7 Pound Close, Yarnton, Oxfordshire, OX51QG
+44-770-304-0079
info@debutinfotech.com
Canada
Debut Infotech Pvt Ltd
326 Parkvale Drive, Kitchener, ON N2R1Y7
+1-708-515-4004
info@debutinfotech.com
INDIA
Debut Infotech Pvt Ltd
Sector 101-A, Plot No: I-42, IT City Rd, JLPL Industrial Area, Mohali, PB 140306
9888402396
info@debutinfotech.com




Leave a Comment