Table of Contents
Home / Blog / Coin Development
Security Tokens vs. Utility Tokens Explained: Key Differences You Should Know
July 15, 2025

July 15, 2025
Have you ever visited a cryptocurrency exchange website and been confused by the myriad of tokens present? Amid thousands of digital assets in the market, one of the most important distinctions to know is the difference between utility token vs security tokens, which is likely to determine compliance and investment success.
As a matter of fact, a recent Chainalysis report revealed that close to 70% of retail crypto investors cannot distinguish between token types, which is a reason why they make uninformed decisions and subject themselves to legal risks.
Meanwhile, the international tokenization market is expected to reach the mark of more than $16 billion by 2030, with a growing number of people using blockchain in financial, real estate, and asset-management.
What then is really the difference between a utility token and a security token, and why is it important that developers, token development companies, investors, and businesses take note of this? Let’s break it down.
Understanding Tokens in the Crypto Ecosystem
A token, as it relates in blockchain and digital finance, is a unit of value that a project or organization issues, usually on top of an existing blockchain such as Ethereum or Solana. In sharp contrast to coins, which can only exist upon their respective blockchains (e.g., Bitcoin or Ether), tokens can be viewed as programmable assets or access rights that are deployed on decentralized networks via smart contracts.
Tokens may be used in very different ways, some to access a platform, or to signify a claim over a digital or physical asset, or in some cases, even act as governance mechanisms over a decentralized protocol. Understanding the distinction between a utility token vs security token is crucial in this context.
These are usually released in an Initial Coin Offering (ICO), which is more or less analogous to a common Initial Public Offering (IPO). Specialized ICO Development services are often employed to facilitate this process. But, in contrast to equity, the participants of ICO get tokens, which can subsequently be utilized in the ecosystem of the issuer.
In contrast to IPO shares, tokens may or may not confer ownership, but may provide utility, including accessing software or services on a decentralized network, or voting on decisions across a network.
Simply put, tokens can be regarded as a flexible digital tool, which comprises an investment opportunity, rights to access (access rights), and software useability (all under blockchain infrastructure).
Related Blog: Role of Tokens in Exchanges
Turn Real-World Assets into Digital Goldmines
Unlock liquidity, transparency & new markets with our tokenization solutions. Discover how we transform assets into tradable digital tokens, securely and scalably.
Understanding Security Tokens
Security tokens are assets in the form of blockchain technology that reflect ownership in tangible or real-world financial assets, like company shares, real estate, or revenue streams. As opposed to utility tokens, security tokens are characterized as investments and are subjected to federal securities laws, highlighting a key distinction in the utility token vs security token debate. They are issued based on the value of an external, tradeable asset and are intended to entitle the holder to a legal right, such as dividends, paying interest, or voting.
Security tokens are generally created through STO Development under Security Token Offering (STOs), a regulated fundraising system that aims the goal of offering investor protection and transparency. They can be safely, effectively, and legally used to invest in digital assets when they are correctly issued and do comply with the regulations.
Key Features of Security Tokens
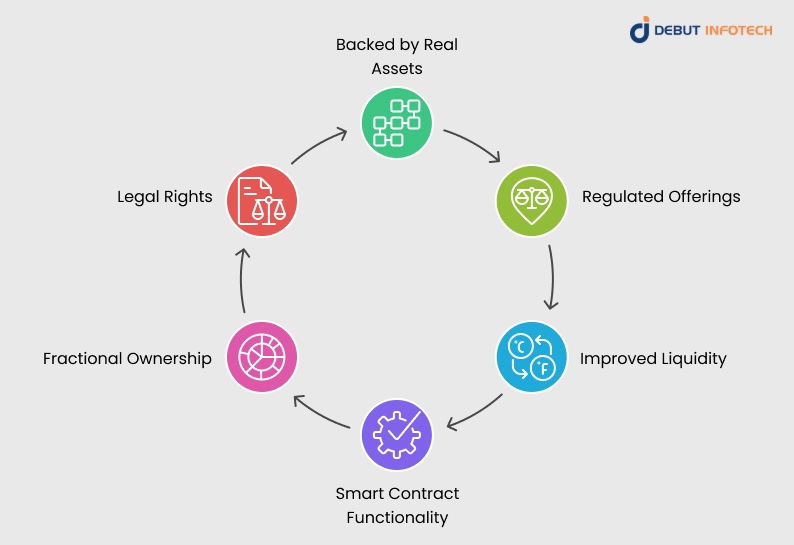
- Backed by Real Assets: Represent equity, debt, or other physical financial instruments.
- Regulated Offerings: Have to meet the security laws, including Regulation D, Regulation A+, or Regulation S in the US.
- Improved Liquidity: Facilitates secondary trading of tokens on licensed exchanges, which convert traditionally illiquid assets in a way that they can be more readily bought and sold.
- Smart Contract Functionality: Automates things such as payment of dividends and change of ownership.
- Fractional Ownership: Enables partial investment, thus making high-value assets more affordable.
- Legal Rights: May award holders dividends, shares of profits, or payment of interest or rights of the government.
Security Token Compliance
Security tokens have to comply with regulations like the Howey test that identifies an asset as security. By satisfying this condition, tokens will fall under the Securities Act of 1933 and the Securities Exchange Act of 1934, and be subject to registration or must fit within an exemption.
- Regulation D: Accommodates small amounts of general solicitation to existing accredited investor offerings.
- Regulation A+: Permits offers on up to a sum of $50 million to both non-accredited as well as accredited investors, subject to SEC approval.
- Regulation S: Regulates the offering that is made outside the U.S. and exempts it from registration within the U.S., yet the foreign laws are not excluded.
Benefits of Security Tokens
- Enhanced trust through legal compliance
- Automated operations via blockchain and smart contracts
- Lower transaction costs and reduced reliance on intermediaries
- Wider access to investment opportunities across borders
Challenges to Consider
- Regulatory Complexity: Understanding international laws is complex and time-consuming.
- Market Maturity: The adoption is in a continuous upward curve, and the infrastructure is shifting.
- High Setup Costs: Compliance costs may be high in terms of legal, technical costs.
- Custody & Security: Asset security is one of the major concerns.
Although utility tokens help to gain access to a platform, security tokens are the real-world value of billion-dollar investments identified as an investment contract. As the idea of tokenization picks up, security tokens are emerging as a medium between the current centralized system of finance and a decentralized future.
With their ability to provide transparency, compliance, and their inherent efficiency, they can transform the way investors are interacting with assets therefore creating a more transparent, liquid, and programmable financial market, especially when developed with an experienced crypto token development company.
Understanding Utility Tokens
Utility tokens represent any digital asset that gives users access to a certain service or product on a blockchain-based system. Unlike security tokens, utility tokens are not supposed to indicate ownership or to serve as a typical investment tool. Rather, they serve more like digital coupons that allow one to interact with the functions or offerings of a platform.
These tokens are usually issued in defining a fundraising exercise like the initial Coin Offering (ICOs) or Token Generation Events (TGEs), often facilitated by IDO development companies for newer launch models. They help drive activity in the ecosystem through unlocking a service, getting a discount, or being part of the platform governance. Since they are not set up as securities to make profits but are set up according to utility, they can escape security regulation with proper design.
Common examples of utility tokens are Filecoin, Siacoin, and Civic.
How Utility Tokens Work
Utility tokens have a function-oriented design within a particular blockchain environment. Here’s how they typically work:
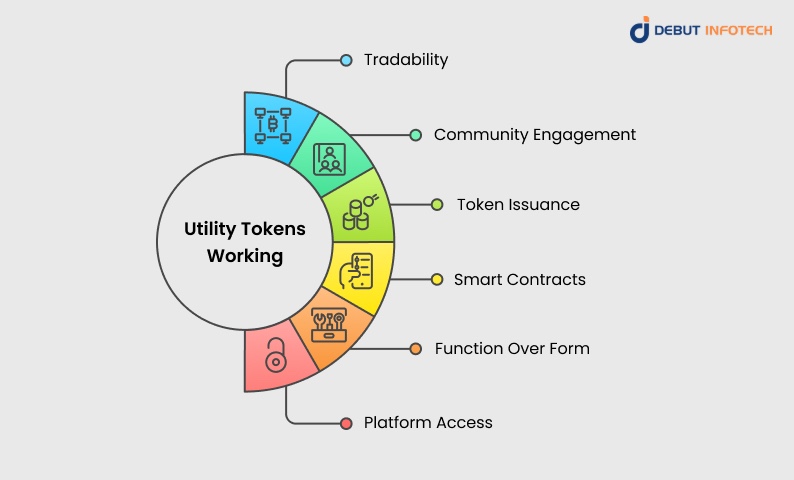
- Tradability: Due to the fact that utility tokens are cryptocurrencies, they may also be exchanged in blockchain exchanges. Their price is dependent on market forces like demand, platform usage, and token supply.
- Community Engagement: Certain platforms would provide governance rights where the holders of tokens get a say in the updates to the system, policy alterations, or development pathways.
- Token Issuance: During an ICO or TGE, there is usually the issuance of utility tokens. They may be bought by interested participants in popular cryptocurrencies like Bitcoin or Ethereum.
- Smart Contracts: These tokens are frequently built on smart contracts, self-executing terms programmed into the blockchain, which govern their generation, distribution, and terms of operating with them. Common standards like ERC20 Token development are often used for utility tokens on the Ethereum blockchain.
- Function Over Form: Utility tokens are not a source of ownership, dividends, or equity. They are valuable because of what users can use them for on the platform.
- Platform Access: A utility token is typically used to enable one to access the services or functionalities of a decentralized application (DApp) or a blockchain product.
Roles of Utility Tokens
There are several important roles that utility tokens serve in blockchains. Some of which include:
- Access to Platform Services: They are a way of accessing certain services, functions or apps.
- Operational Functionality: Smart contracts prescribe the functionality of the token in the ecosystem and implement the rules of use.
- Exchange Compatibility: These tokens are frequently traded in crypto exchanges and thus they are available to any person anywhere in the world.
- Fundraising Mechanism: Utility tokens are used to raise funds and they do this through ICOs, TGEs, or IEO Development.
- Non-Investment Classification: In contrast to security tokens, utility tokens do not establish financial ownership and right to profits.
- Governance Participation: Governance rights are included in some projects, so that token holders can participate in the voting process regarding any significant decisions.
Challenges and Limitations of Utility Tokens
Though utility tokens are very advantageous, they also have several challenges. Some of which include:
- Investor Risk: Most ICOs have been tied to fraud or failed projects, putting the token investors at risk of financial losses (Modern alternatives like services from IDO development companies aim to mitigate these risks through more secure, decentralized launch mechanisms).
- No Intrinsic Value: Utility tokens are not usually sold with independent value, but instead their value is pegged on the success of their related platform.
- Regulatory Ambiguity: Utility tokens are usually in a regulatory grey area, often hinging on the distinction in utility token vs security token debate. The status of whether they are or are not securities may be complex and depend on the jurisdiction.
- Market Volatility: There is also the possibility of prices going high because of market sentiment or hype, or changes in the popularity of platforms.
- Limited Adoption: Without a base of users, the functionality and relevance of a platform’s utility token can decrease.
- Technological Dependency: They rely on the stability and functionality of the blockchain network on which they operate.
- Saturated Market: As thousands of projects around the world launch tokens, it becomes harder to emerge and attract traffic.
Utility tokens will continue to be an effective mechanism of digital service provision and community interaction in a blockchain platform. Nevertheless, their design, deployment, and control need to be well managed to provide long-term sustainability and confidence in the ecosystem.
Utility Tokens vs. Security Tokens: Key Differences Explained
It is essential to understand the distinction between utility and security tokens to be successful in the crypto and blockchain environment. The purposes of these tokens differ, and they are subject to divergent regulatory treatments, which affect usage, investment, and legal commitments. Security Tokens and Utility Tokens can be distinguished based on the following:
Purpose and Function
- Security Tokens are the digitized form of tokens of ownership in real-based assets, such as the stocks of a company, real estate, or any other type of financial instrument. Their main purpose is investment, where holders anticipate financial rewards to be paid other than an increase in the value of the shares.
- Utility Tokens aim to open access to a particular product, service, or functionality on a blockchain platform. They act as in-store currencies, enabling people to use the functionalities of the platform. This payment function is a core aspect of utility tokens, distinct from security tokens, and is also central to specialized areas like stablecoin development services.
Underlying Value
- Security Tokens are resource-based assets, or asset-based securities, so they have an inherent value linked to the performance of those underlying assets.
- Utility Tokens exist because of their usefulness on a particular platform. The token demand is determined by the popularity and usability of the blockchain service it covers.
Regulatory Oversight
- Security Tokens are covered by rigorous securities laws in most jurisdictions. They have to adhere to legal frameworks and usually undergo well-defined procedures such as Security Token Offerings (STOs). Their status largely depends on the Howey Test used to guide their determination as to whether they are part of an investment contract by use of the token.
- Utility Tokens operate in a more ambiguous regulatory environment. While some may eventually be classified as securities, many are not subject to the same scrutiny. They frequently get issued through Initial Coin Offerings (ICOs) or Token Generation Events (TGEs) which can have less compliance requirements involved. Projects seeking faster deployment might explore options like a white label AI Token solution.
Issuance and Investment Perspective
- Security Tokens are the type of tokens that are issued in strongly regulated sources and are attractive to investors seeking long term and asset-backed yields.
- Utility Tokens are generally more of a speculation. They can be issued in the form of ICOs or TGEs (sometimes involving a BEP20 Token), which bring an opportunity to get in early on innovative platforms but provide greater volatility and risk.
Real-World Examples of Utility and Security Tokens
Security Tokens in Action
The security tokens are transforming the issuance, ownership, and trade of traditional assets on the blockchain.
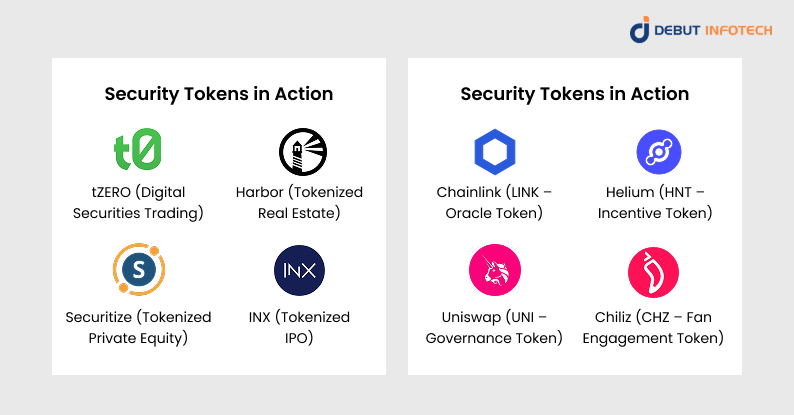
- tZERO (Digital Securities Trading): tZERO, supported by Overstock.com, is a regulated security token trading platform (including a payment launchpad gateway) covering such security tokens as tokenized shares and debt instruments.
- Harbor (Tokenized Real Estate): Harbor specializes in the tokenization of commercial real estate and nonpublic securities. It allows fractional ownership and efficient compliance associated with property investments.
- Securitize (Tokenized Private Equity): Issuance and management of digital securities is displayed within the platform Securitize. It has tokenized equity of private companies and received investment from Coinbase and Blockchain Capital.
- INX (Tokenized IPO): INX appeared in the news because it became one of the first companies to hold a fully registered tokenized IPO in the U.S. and raised more than 80 million in its security token.
These projects are pointing to the increased acceptability of security tokens in capital markets, which allows investors to be more flexible and transparent.
Utility Tokens in Practice
Utility tokens are easily used on blockchain platforms, such as making a transaction or unlocking a service.
- Chainlink (LINK – Oracle Token): The Chainlink network allows payment through LINK to buy services, which allows them to connect smart contracts to the real world, i.e., weather or price information.
- Helium (HNT – Incentive Token): HNT is given to the people who share wireless coverage by utilizing the decentralized IoT infrastructure of the Helium network.
- Uniswap (UNI – Governance Token): UNI token-holders have a say in major protocol changes, fee principles, and governance suggestions at the Uniswap decentralized exchange (DEX).
- Chiliz (CHZ – Fan Engagement Token): Fan tokens on such websites as Socios.com can be purchased with CHZ, where users can vote on club decisions and receive rewards as sports fans.
These illustrations demonstrate how utility tokens strengthen interaction and motivate action in the blockchain-based ecosystems. Unlike meme coin development, which prioritizes virality over utility, these tokens solve concrete problems.
Ready to Tokenize Your Assets? Let’s Build Your Future.
Our experts craft tailored tokenization strategies from compliance to deployment. Get a free roadmap to unlock asset potential.
Final Thoughts
The point of difference between security tokens and utility tokens is vital to know because it influences the regulation consideration, investment strategies, and even platform building. As the blockchain technology grows further and the use becomes more widespread, the ability to determine the purpose and the legal status of each type of token will be essential. As an investor, developer, or policy-maker, having this information helps you make more informed decisions and contribute more ethically to the new world of crypto.
Frequently Asked Questions (FAQs)
A. Utility tokens are mainly used to gain access to a platform’s features or services. In contrast, security tokens signify ownership in an asset and often come with the potential for financial returns. While security tokens must adhere to strict regulatory requirements, utility tokens typically operate with fewer legal constraints.
A. Utility tokens are digital assets issued primarily to support the development of a cryptocurrency project and are later used to access specific goods or services within that ecosystem.
A. In the context of computer privacy and virtual currency, a security token in crypto refers to a digital asset, often an altcoin or a token built on another blockchain, that represents ownership, utility, or value issued by a company. These tokens are managed through smart contracts and distributed ledgers, allowing them to function as programmable assets or access rights within a decentralized system.
Our Latest Insights



Leave a Comment